Introduction
This documentation will provide various resources reference for our partners to manage information on SG Lite. This documentation provides the following functionalities for our partners:
- Customer management
- Inventory management
- Order management
- Item management
- Product management
- Payment method
- Shipping method
- Channel method
API Endpoint
Header:
Content-Type : application/json
Access-Token : YOUR-API-TOKEN
https://opensgapi.sitegiant.co/api/v1
API call limit
Automated tasks that pause and resume are the best way to stay within the API call limit because you don't need to wait while things get done. This article will show you how to tell your program to take small pauses to keep your app a few API calls shy of the API call limit and to guard you against a 429 Too Many Requests error.
Avoiding 429 Too Many Requests errors
You can check how many calls you've already made using the SiteGiant header that was sent in response to your API call. Some things to remember:
- X-RateLimit-Remaining lists how many calls left that you can made for that particular shop.
- X-RateLimit-Limit lists the maximum limit calls that you can made for that particular shop.
Postman Collection
Import our Postman collection for easier integration with our API
Our API Postman collection is available for importing. The collection includes the REST API for all of our endpoints.
The collection will be updated periodically, so keep checking back. Keep in mind that you'll need to import the collection again when a new version of the REST API is released in order to get any new updates.
To view, import, or fork our API collection in Postman, click the button below:
Webhook
Configure a webhook
The trouble with testing your webhooks through the API is that you need a publicly visible URL to handle them. Unlike client-side redirects, webhooks originate directly from the server. This means that you cannot use the following as an endpoint in your testing environment:
- Localhost
- "Fake" domains like www.example.com
- Sitegiant domains (i.e. sitegiant.co and www.sitegiant.co)
Receive a webhook
Once you register a webhook URL with Sitegiant, we will issue a HTTP POST request to the URL specified every time that event occurs. The request's POST parameters will contain JSON data relevant to the event that triggered the request.
Sitegiant verifies SSL certificates when delivering payloads to HTTPS webhook addresses. Please ensure your server is correctly configured to support HTTPS with a valid SSL certificate. There will be a maximum of 3 retries for a webhook request. The timeout period for each request is 10 seconds.
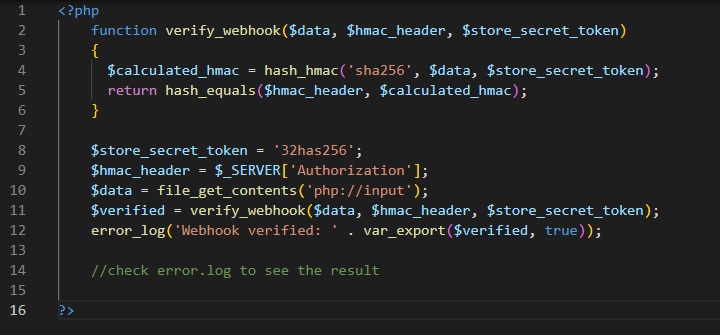
Verify a webhook
Each webhook request includes Authorization header, which is generated using the store secret token along with the data sent in the request.
To verify that the request came from Sitegiant, compute the HMAC digest according to the following algorithm and compare it to the value in the Authorization header. If they match, you can be sure that the Webhook was sent from Sitegiant and the data has not been compromised.
Below is a simple example in PHP version of how to verify a webhook request.